Frequently Asked Questions
1. To register, visit the registration page here.
2. On the home page select Sign Up.
3. You will be redirected to the Sign Up page. Please fill in the details and have a valid and active phone number to
receive an OTP for verification.
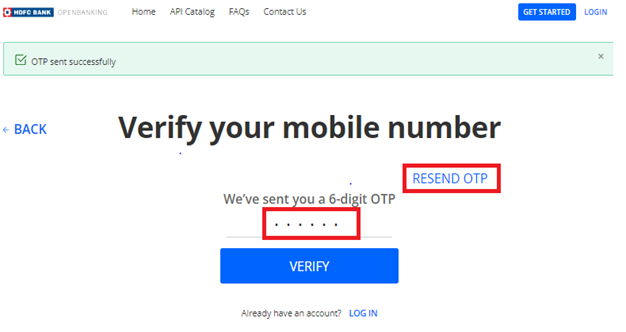
4. Please enter your OTP for verification. You have upto 3 tries to receive an OTP.
5. Once you have successfully registered on our portal you and your manager will receive an email notification with a link redirecting you to a page where you can login and set your password.
6. Keep in mind that the link expires in 24 hours and you will have to repeat the registration process again.
7. On a successful password reset you can login and Try Out our API’s using our static sandbox environment.
8. Your registration application is still in pending status until we approve it. Once approved you will receive an email stating you can login to create applications and subscribe to API’s as described in the section here Accessing APIs
In case of activation email not received or if activation link expires, Partner can raise forgot password request providing the email given while registration.
Yes, multiple developers of a single organization can have accounts as their emails are unique.
You can refer to this link- https://codebeautify.org/
You can refer to this link- https://www.xml.com/pub/a/2001/08/08/xmldsig.html
Yes, the platform will show the "Signature verification failed" error if the signed payload value and original payload value have minor differences.
You can refer to this link-https://www.base64encode.org
You can refer to this link- https://8gwifi.org/RSAFunctionality?keysize=2048
No, you can not use No Padding for both encryption and decryption algorithms as that would result in a "Decryption failed" error.
Yes, algorithms mentioned in HDFC Bank's user manual are as per HDFC Bank API security guidelines and have to be used in that exact manner. To put it simply, symmetric encryption uses the AES/CBC/PKCS5Padding algorithm, while asymmetric encryption uses RSA/ECB/PKCS1Padding.
Yes, it is mandatory for Partners to utilize a 32-byte random (alpha-numeric) key to symmetrically encrypt the complete API request payload. A new value of this 32-byte random key needs to be generated for each API requested by the Partner.
Yes, it is mandatory to set a unique transaction ID every time to identify a JSON wrapper request.
HDFC Bank's SSL certificate public key is required. Any other public key will result in a "Decryption failed" error.
IV stands for Initialization Vector, which needs to be passed by appending the same at the beginning of the original request payload, before performing the encryption. If the IV is not being used for AES encryption, then 16-byte random characters need to be specified at the beginning of the original request payload before performing the encryption.
The following special characters are restricted as API requests with these characters trigger Code Injection or SQL Injection validations on the API Platform. It is recommended that the Partners replace these special characters with a space.
& (ampersand)
' (apostrophe)
, (comma)
. (full stop)
- (hyphen)
/ \ (forward and backward slash)
! (exclamation)
You can use the Client ID as Username and the Client Secret as Password.
No, Partners need to generate a new OAuth token for every request.
No, all HDFC Bank APIs do not utilize OAuth. HDFC Bank has classified a few APIs under the high criticality section, especially APIs that involve financial transactions and only those APIs utilize OAuth. A separate API has been published for generating a one-time-use OAuth token, which requires valid values for Client ID and Client Secret to generate a token. The token needs to be sent as part of the request of the main API.
If the Partner does not provide an API Key or mistakenly provides an incorrect one, then they receive an error stating "Invalid API Key".
You can specify "application/json" under the content type field.
You can refer to this link- application/www-form-url encoded