Frequently Asked Questions
HDFC Bank Developer PKI
An X.509 Public Key Infrastructure (PKI) is implemented by HDFC Bank for issuing and managing certificates to be used in conjunction with HDFC APIs for SSL Handshake, Payload Encryption and Digital Signature Verification (wherever applicable). This PKI consists of a hierarchy of entities called CAs that issue certificates to “Subscribers” (that is, end-entities or other CAs) within the hierarchy. The term PKI is used to refer to all of the Subscribers from the root CA all the way down to the lowest level end-entity.
This page provides the HDFC Bank Developer Platform public certificates used to identify HDFC Bank API endpoints.
Click here to download latest certificate.
1. To register, visit the registration page here.
2. On the home page select Sign Up.
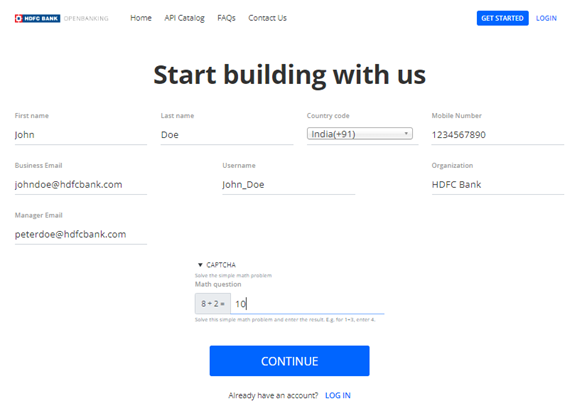
3. You will be redirected to the Sign Up page. Please fill in the details and have a valid and active phone number to
receive an OTP for verification.
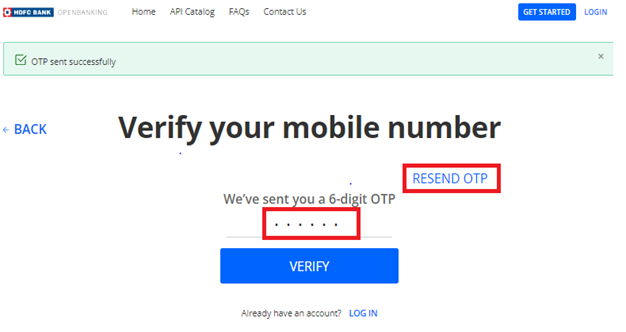
4. Please enter your OTP for verification. You have upto 3 tries to receive an OTP.
5. Once you have successfully registered on our portal you and your manager will receive an email notification with a link redirecting you to a page where you can login and set your password.
6. Keep in mind that the link expires in 24 hours and you will have to repeat the registration process again.
7. On a successful password reset you can login and Try Out our API’s using our static sandbox environment.
8. Your registration application is still in pending status until we approve it. Once approved you will receive an email stating you can login to create applications and subscribe to API’s as described in the section here Accessing APIs
All HDFC Bank' APIs utilize two-way SSL, also known as mutual authentication, for better security. In two-way SSL authentication, both the client and server side need to authenticate and validate each other's identity. Hence, to achieve two-way SSL, Partner's certificate needs to be added to the Bank platform’s certificate truststore and the Partner needs to do the same. Note: Partner should only send the Public Key of the CA signed SSL certificate to the Bank.
HDFC Bank's security policies block certificates sent on email. Therefore, Partners are requested to change the extension of the certificate files to .txt before sending certificates over email.
HDFC Bank welcomes innovation and constantly continues to change the way we do business. With Embedded Finance and Open Banking taking central stage in the current Banking Environment, HDFC decided to open up the API stack for new age businesses to take advantage of our offerings and help businesses launch products quickly.
If you/your corporation has an existing relationship with the bank then please reach out to your Relationship Manager or contact us.
Our API Catalog page can show you what APIs are available based on product. In case you are unable to locate the API’s that you are interested in you can contact us with a brief description of your business case. We will review your business case and will revert back.
Once you have successfully registered you can log into the HDFC Developer Portal to access workflows and technical documentation related to our API Products. You can locate the documentation within the API catalog. Within the API catalog you will find your API and can locate the user manual on selecting the Test Now section.
Try it out is a feature to test APIs to understand the request response of an API. Users can find what parameters are used, possible return codes along with their meaning. On successful account creation one can access the Sandbox environment to view sample request responses.
Users can only upload leaf certificate on portal. They cannot upload root and intermediate certificates. Also, user should not upload self-signed and untrusted certificates.
See below for different types of certificates:
Leaf Certificate : Leaf Certificate will have a full chain of certificates.
Root, Intermediate and Leaf (Main) Certificates
Intermediate Certificate : In Intermediate certificate will have a two chain of certificates.
Root and Intermediate
Root Certificate:- In root certificate only one chain of certificate.
Root certificate
We can upload the leaf or server certificate in .cer, .crt and. pem format.
Please use the sample data provided in try it out feature. To reach this page, navigate to API catalog and click on API Product and then click on TRY NOW of respective API.
1. Select “Import” button.
2. Select “curl” from menu option as shown in below screenshot
Note: Certificate to be uploaded is Leaf certificate
3. Select “OAuth Curl Command.txt”. Please save the below command in text file
curl --location --request POST 'https://api-uat.hdfcbank.com/auth/oauth/v2/token?scope=XXXX=client_credentials' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--header 'Authorization: Basic QUFBQUE6QkJCQkI=' \
--header 'Cookie:
ci_session=a%3A4%3A%7Bs%3A10%3A%22session_id%22%3Bs%3A32%3A%229d68e965a66c9dbc44a30b8c94a6efc5%22%3 Bs%3A10%3A%22ip_address%22%3Bs%3A14%3A%22175.100.161.32%22%3Bs%3A10%3A%22user_agent%22%3Bs%3A21%3A%22 PostmanRuntime%2F7.28.4%22%3Bs%3A13%3A%22last_activity%22%3Bs%3A10%3A%221641471329%22%3B%7D0dfae2f559 34b0591850fe837c09a163'
Note:
Scope value should be value present in portal
QUFBQUE6QkJCQkI=' is the key and secret encoded value
4. Select Params section to add Scope and Grant_type values.
Note: Scope value must be same that you mentioned while creating Application as shown below:
5. Select “Basic Auth” under Authorization tab and enter Username & password
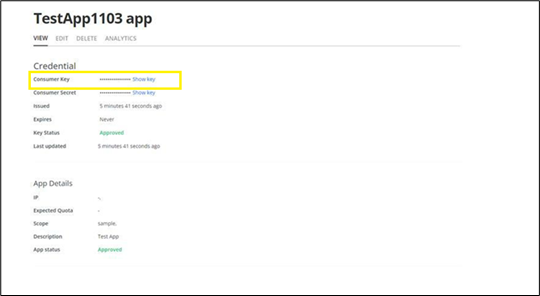
Note : Username is your 'Consumer Key' and Password is your 'Consumer Secret' that you receive after creating the application as shown below:
Pre-requisite: IP needs to be updated in portal while creating apps and these IPs should be static and approved.
Scenario 1: If IP is not whitelisted, user will get unauthorized IP error.

Apigee App:
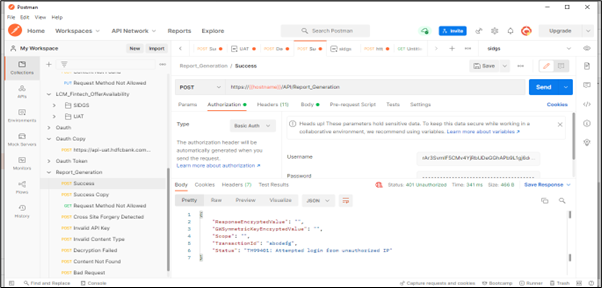
Scenario1:
Cause:
API Key is not passed in headers tab while making a request in postman.
How to identify?
1. Open postman.
2. Go to Headers tab.
3. Check whether Consumer Key and its value is present in headers tab as 'Key' and 'value' being alphanumeric taken from portal.
Below is the pictorial representation
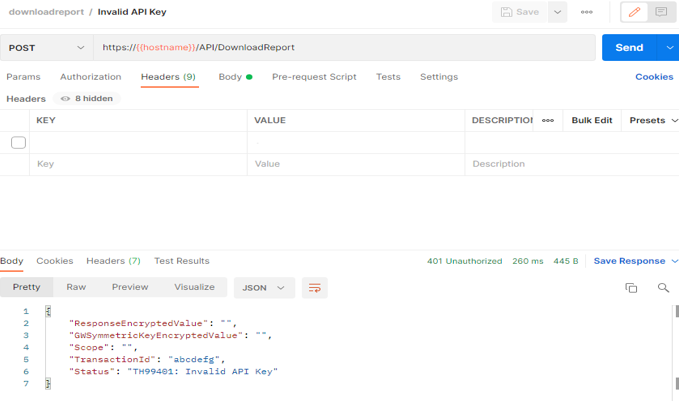
Scenario2:
Cause:
Incorrect Consumer Key is passed as API Key in Headers Tab.
How to identify?
1. Open postman.
2. Go to Headers Tab.
3. Check whether APIKEY and its value present in headers tab are same as that of Consumer Key on portal..
Scenario 1: If partner is using HTTP in place of HTTPS.
Scenario 2: If SSL option is checked in postman settings.
Scenario 1: If partner's public leaf certificate uploaded in portal during application creation doesn’t match with the leaf certificate added in postman settings when request is made.
Prerequisites:
I. Partner should share their CA signed (Root and intermediate certificate ) to HDFC for whitelisting.
II. Leaf or Server certificate should be uploaded in portal when application is created and HDFC Bank team must approve.
III. Partner should upload the leaf certificate and private key in postman settings tab before making any request.
Scenario 2: If the Partner does not provide a client certificate while making a request to an API that utilizes two-way SSL.
Pre-requisites:
a. Partner Public certificate (a chain of root, intermediate and leaf ) should be CA signed.
b. Partner Public certificate (a chain of root, intermediate and leaf) needs to be whitelisted at bank end.
Note: Certificate to be uploaded in postman is Leaf certificate
Adding certificate in postman.
- Open postman app.
- Click on settings icon.
- Click on Add Certificate link under certificates tab as shown below.
4. Adding Certificates:
There are two methods of adding the certificates based on the availability of required certificate formats.
Pre-requisites:
a. Your Public leaf certificate
b. Your Private key
Step1: Enter the Hostname as “api-uat.hdfcbank.com” and port as “443”
Step2:
A. “PFX file” format: Create .pfx file format using your public certificate and private key.
1. Import the file,
2. Enter the password in “passphrase” field that you created while generating the .pfx file format.
3. Click on add button.
B. “CRT file” format:
1. Import Your Public leaf certificate in “CRT file” section.
2. Import Your Private key in “KEY file” section.
3. Click on add button
Note:(No need to enter passphrase)
Below screenshot depicts how PFX file is used to add the certificate
Below screenshot depicts how public certificate and private key is used to add certificate.
5. Click on add button. You will see certificate added in Certificates tab.
Criticality: There are 9 types of Criticalities
- Medium (5 Fields Wrapper)
- Medium With DS (5 Fields wrapper)
- High (5 Fields wrapper)
- Medium with ID token (6 Fields wrapper)
- Medium With DS with ID token (6 Fields wrapper)
- High with ID token (6 Fields wrapper)
- Medium (7 Fields wrapper)
- Medium With DS with ID token and IDCOM token (7 Fields wrapper)
- High with ID token and IDCOM token (7 Fields wrapper)
5 field wrappers:
Fields for Medium proxy:
- "RequestEncryptedValue",
- "SymmetricKeyEncryptedValue"
- "Scope" Value given in portal and params in postman should be same
- "TransactionId" -Should be alphanumeric
- "OAuthTokenValue" value will be empty
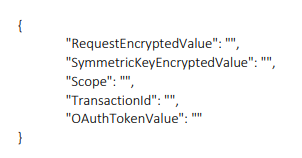
Fields for Medium with DS proxy:
- "RequestSignatureEncryptedValue",
- "SymmetricKeyEncryptedValue"
- "Scope" Value given in portal and params in postman should be same
- "TransactionId" -Should be alphanumeric
- "OAuthTokenValue" value will be empty
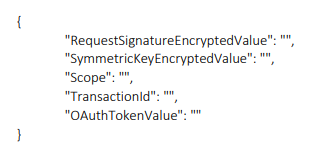
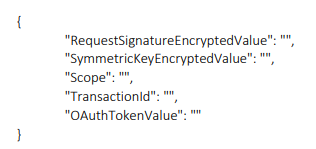
Fields for High proxy:
- "RequestSignatureEncryptedValue",
- "SymmetricKeyEncryptedValue"
- "Scope" Value given in portal and params in postman should be same
- "TransactionId" -Should be alphanumeric
- "OAuthTokenValue" value should be present
6 Field wrapper:
Fields for Medium proxy with ID token
- "RequestEncryptedValue",
- "SymmetricKeyEncryptedValue"
- "Scope" Value given in portal and params in postman should be same
- "TransactionId" Should be alphanumeric
- "OAuthTokenValue" value will be empty
- "Id-token-jwt" Depending on ID token generation or verification, it can have value or can be empty
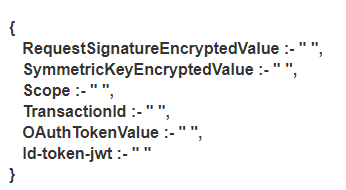
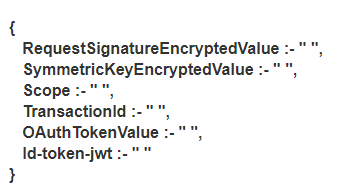
Fields for Medium with DS proxy with ID token
- RequestSignatureEncryptedValue",
- "SymmetricKeyEncryptedValue"
- "Scope" Value given in portal and params in postman should be same
- "TransactionId" Should be alphanumeric
- "OAuthTokenValue" value will be empty
- "Id-token-jwt" Depending on ID token generation or verification, it can have value or can be empty
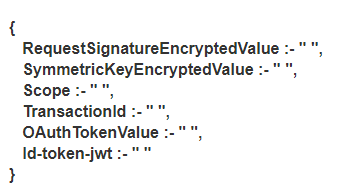
Fields for High proxy with ID token
- RequestSignatureEncryptedValue",
- "SymmetricKeyEncryptedValue"
- "Scope" Value given in portal and params in postman should be same
- "TransactionId" Should be alphanumeric
- "OAuthTokenValue" Value will be present
"Id-token-jwt" Depending on ID token generation or verification, it can have value or can be empty
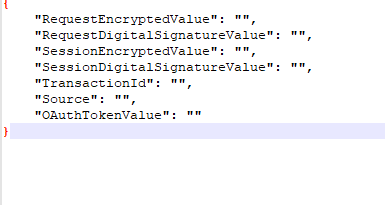
7 Fields wrapper:
Fields for Medium proxy with 7 field standard wrapper
- "RequestEncryptedValue",
- "RequestDigitalSignatureValue", value will be empty
- "SessionEncryptedValue" same as "SymmetricKeyEncryptedValue"
- "SessionDigitalSignatureValue" value will be empty
- "TransactionId" Should be alphanumeric
- “Source” same as “Scope”
- "OAuthTokenValue" value will be empty
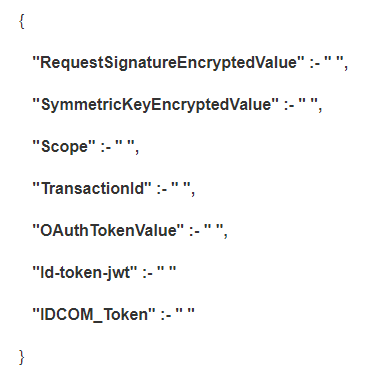
Fields for Medium with DS proxy with ID token and IDCOM token
- “RequestSignatureEncryptedValue",
- "SymmetricKeyEncryptedValue"
- "Scope" Value given in portal and params in postman should be same
- "TransactionId" Should be alphanumeric
- "OAuthTokenValue" value will be empty
- "Id-token-jwt"
- “IDCOM_Token”
Fields for High proxy with ID token and IDCOM token
- “RequestSignatureEncryptedValue",
- "SymmetricKeyEncryptedValue"
- "Scope" Value given in portal and params in postman should be same
- "TransactionId" -Should be alphanumeric
- "OAuthTokenValue" value should be present
- "Id-token-jwt"
- “IDCOM_Token”
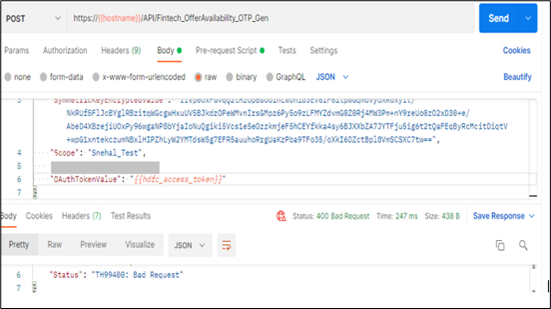
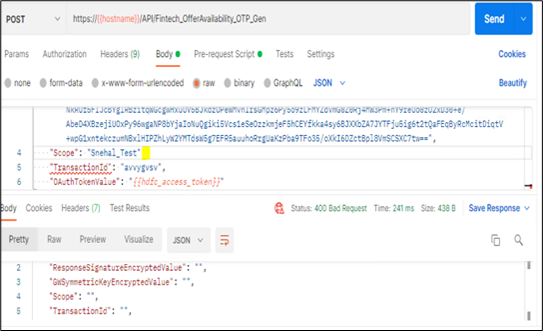
Scenario 1: If any of the mandatory wrapper fields are missing.
In below example, “TransactionId” field is missing while making the request.
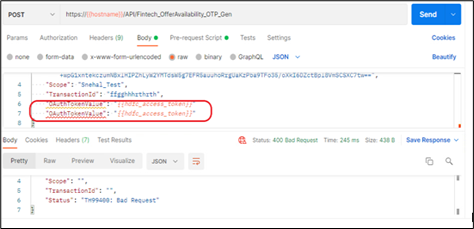
Scenario 2: If there are duplicate wrapper fields
In below example, “OauthTokenValue” field has been used twice.
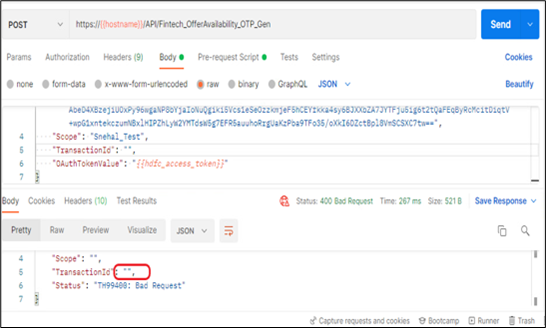
Scenario 3: If any of the mandatory wrapper field “values” are blank
In below example, “TransactionId” field's value is blank
Scenario 4: If any of the Wrapper Fields name is incorrect.
In below example, “RequestSignatureEncryptedValue” field name is incorrect
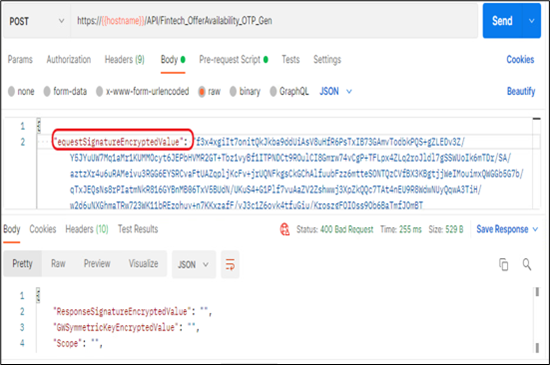
Scenario 5: If separator is missing among wrapper fields.
In below example, comma is missing next to value of the “Scope”
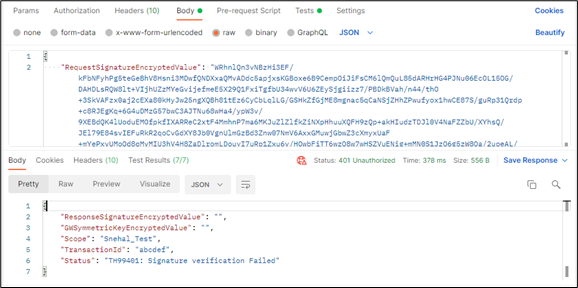
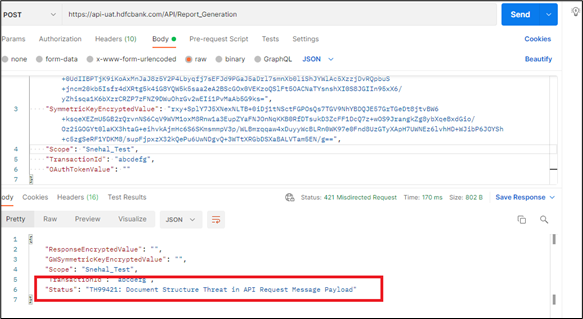
Scenario 1: If Incorrect payload is passed (Payload is not digitally signed and encoded with partner's private key)
Scenario 2: If incorrect logic is used to sign the payload.
Scenario 3: If incorrect payload is signed.
Below screenshot depicts the error format
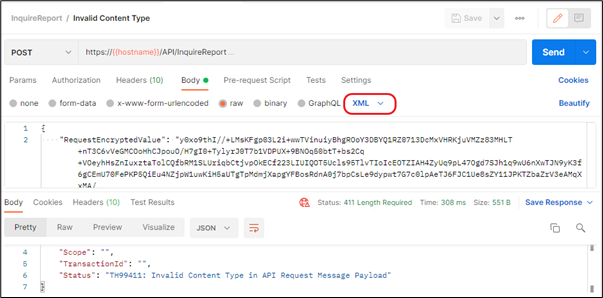
Scenario1:
Cause:
If inconsistent payload format is selected while making the request.
How to identify?
1. Open postman.
2. Go to Body section, click on raw tab.
3. Select the format of the paylaod.
For Instance: If the Payload is in json format and user selects the xml format, API Gateway throws the below error (Invalid Content Type).
Scenario 2:
If correct content-type value is not passed in headers while making the request.
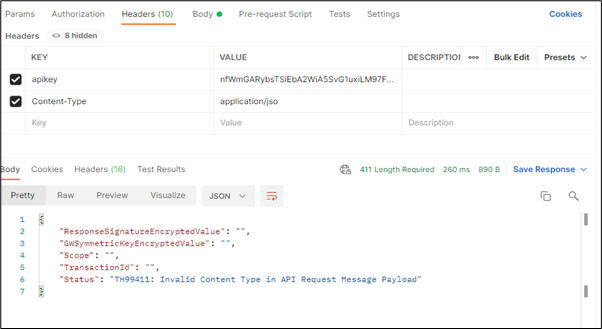
Scenario 1: If incorrect encryption logic is used.
Scenario 2: If symmetric key is not of 32 bytes.
Scenario 3: If symmetric key contains special characters. Only alphanumeric is allowed in symmetric key field.
Scenario 4: If IV + Signature is not appended.
Scenario 5: If IV Value contains special characters. Only alphanumeric is allowed in IV field.
Scenario 6: If incorrect or invalid private key is used.
Scenario 7: If incorrect padding algorithm is used.
Scenario 8: If .net code is used to code encryption-decryption logic. The result would be BASE24 encoded by default. Partner should not encode one more time.
Below screenshot depicts the error structure.
You can subscribe to APIs by creating an application. Think of an application as your API key and secret management. It’s enables you to retrieve access tokens. You can register as many APPS as you like.
Before you can start using HDFC’s APIs, you must first create an application, allowing you to subscribe to services. Your application allows for the generation of a consumer key, consumer secret, and access/authorization token (if needed) to access the APIs. Follow these steps to create an application:
1. Sign into your account using your registered username and Password.
2. Select the Launchpad menu to navigate to the Apps page to create your first app or view apps that have already been created.
a. Create your first app page
b. View the list of created Apps
3. To create a new app follow the procedure below:
a. APP Name, API Products, IP, Scope and Certificate sections are mandatory for creating any app.
b. App Name: Enter the App name has the limit of 255 characters (Alphanumeric, space, and the following: _ - . # $ %. Must begin with an alpha character) (This input will contain the organisation/ partner name along with the product required as an identifier eg. HDFC_CRMLead)
c. Description: Enter the description has the limit of 225 characters (This input will describe the use case of the partner)
d. Expected Quota: Enter API volumes expected per day.
e. Call-back URL: Optional field (Can be left Blank). A callback URL is a URL that will be invoked by the API method you are calling after it's done.
f. Scope: It is mandatory to mention the scope value as your application would be rejected without it. Kindly enter the organisation / partner name into this field unless specified by Bank Staff otherwise. **While scope field ensures that spaces are not entered, you can separate 2 words with the use of an underscore ‘_’character for the same. e.g. HDFC_Lead.
g. Organization specific Unique value which also allows special characters in it can be passed in scope. Ideally, this value should be a one-word name of your partner organization, without any spaces. Exceptions to this is within the Corporate Payment APIs in the case of fund transfers, IMPS, NEFT & RTGS, where HDFC Bank assigns a specific value to be set as the Scope value.
h. Scope can be a max of 30 characters and one can insert multiple Scope values with comma (,) as a separator.
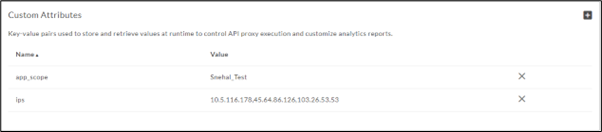
i. IP: Please enter the public Source IPs that would be used for API Integration in this field. Only IP4 range is allowed. (Multiple IP addresses can be separated with commas). Users can give both Static as well as Public IPs. Multiple IP’s are allowed and must be separated by commas “,”.There is a 600 character IP limit and IP ranges are allowed and should follow the following format : 10.10.10.1-10.10.10.100
j. API Products: Select the API Products (Multiple) that you wish to subscribe to. API Products max field length is about 600 characters. If the sum of the selected API Products exceeds 600 characters, please create another App.
k. Certificate: Upload the leaf SSL certificate in base64 encoded format (.cer/.pem) in the App and share Root and intermediate certificates with Bank separately over email.
l. Accept Terms & Conditions and Privacy Policy of HDFC Bank API Banking Program.
m. Select Add App to add the newly created app in the Apps page.
n. You can add as many apps as you want based on your testing needs.
Scenario 1: If the decrypted payload field value exceeds the string length (more than 3000)
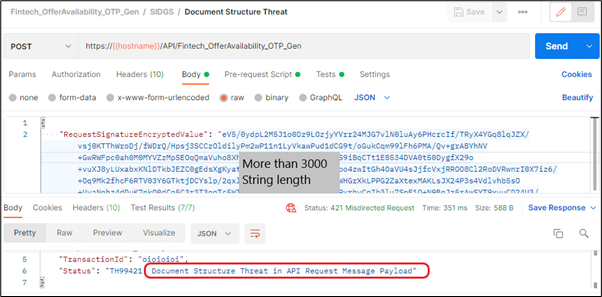
Scenario 2: If request payload exceeds the length of the attribute (Namespaces, Content Depth, Array Size, Array Count)
If length is increased in below mentioned attributes
ArrayElementCount =2000
Container Depth =12
ObjectEntryCount =1200
ObjectEntryNameLength =100
StringValueLength =3000
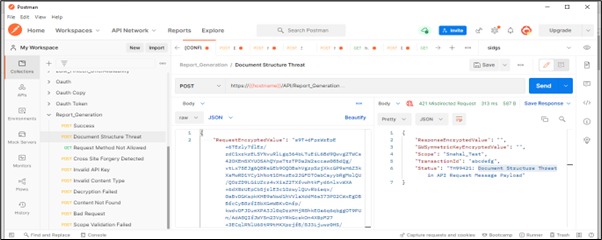
Scenario 3: If the number of objects in the payload is more than 15
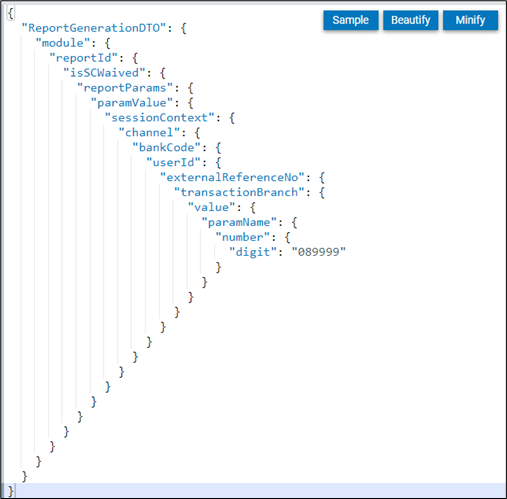
Once you have successfully created an account on the HDFC Bank Developer portal, you can access the Sandbox environment to view sample request responses.
Multiple certificates are not allowed. Per Developer only one certificate can tie up and this can be changed if required.
In case of any technical help, please reach out us using contact us at Contact Us
In case of application rejection, please reach out us using Contact Us
API is a reusable component which developer uses to complete its system. API Product is a bundle of such APIs. APIs in one product are logical in the sense it tries to complete the needs of partner in one product only.
Client ID and Client Secret are unique credentials for each customer application that are required to access any subscribed APIs. As part of the onboarding process on the API Portal, Partners need to create an application. On approval of the application, the Client ID and Client Secret will get generated automatically on the API Portal. The Client ID needs to be utilized as the value of the API key to be sent in the API request header.
In cases where the API indicates that OAuth is needed, the Client ID is additionally used as ‘Username’ while Client Secret is used as the value of 'Password' in the Authorization Headers for the OAuth API call (More details on OAuth API is available in the Technical User Manual).
Client ID and Client Secret can be accessed on the API Portal, within the Partner’s application, in the AUTH tab. These values are unique for each application created by you on HDFC Bank’s API Portal.
Client ID and Client Secret values are generated automatically and partners cannot change them.
Scope associated with the developer application on the dev portal indicates the partner app invoking the API and we generally recommend partners to use their company name or a specific value provided by HDFC.
An API key or application programming interface key is a code that gets passed in by computer applications. The program or application then calls the API or application programming interface to identify its user, developer or calling program to a website.
Application programming keys are normally used to assist in tracking and controlling how the interface is being utilized. Often, it does this to prevent abuse or malicious use of the API in question.
An API key can act as a secret authentication token as well as a unique identifier. Typically, the key will come with a set of access rights for the API that it is associated with.
User can generate N number of API Keys as per their requirements.
Yes, multiple developers of a single organization can have accounts as their emails are unique.
In case of activation email not received or if activation link expires, Partner can raise forgot password request providing the email given while registration.
Partners need to select "Confidential" under the ‘OAuth Type’ field if they are using high criticality APIs. HDFC Bank classifies a few APIs as having high criticality, especially APIs that involve financial transactions. Partners are provided with user manuals that indicate whether OAuth is being used or not. However, most APIs have not been classified as high criticality APIs, and do not use OAuth. For such APIs, the value "None" needs to be chosen under OAuth Type.
Yes, multiple secret keys can be generated. To generate new client secret keys, click on ‘ADD KEY’ button in App details page.
Only SSL certificates signed by a Certifying Authority are accepted by HDFC Bank as the self-signed SSL certificates are not permitted. This is applicable even in a UAT environment.
Yes, Partners will receive a notification from HDFC Bank for providing a renewed certificate, at least a month prior to certificate expiry.
Client ID and Client Secret are unique credentials for each customer application that are required to access any subscribed API. As part of the onboarding process on the API Portal, Partners need to create an application. Once HDFC Bank personnel approve a Partner’s application, the Client ID and Client Secret will get generated automatically on the API Portal.
The Client ID needs to be utilized as the value of the API_Key to be sent in the API request header. In cases where the user manual for the API indicates that OAuth is needed for the API, the Client ID is additionally used as the value of user name while Client Secret is used as the value of User Password for the OAuth API call.
Partners need to create an application as part of the onboarding process on the API Portal. Once HDFC Bank personnel approves your application, the Client Id and Client Secret will be generated automatically on the API Portal. These values can be accessed on the API Portal, within the Partner’s application, in the AUTH tab.
Yes, these values are unique for each application created by you on HDFC Bank’s API Portal.
To subscribe for APIs in the application, go to Application > click on Edit > go to API Management > write API name in search bar > click on Add > click the Save button at bottom.
No, these values are generated automatically and partners can not change them according to their need.
Once you put in the request to reset password for your account, you will receive a link in your mail that you can click directly or copy paste to your browser. This link leads you to a page where you can reset your password. Remember, this link expires after one day and nothing will happen if it is unused.
Once you have made a request to cancel your account, you will receive a mail with a link that will take you to the account cancellation page. Simply click on the link or copy paste it to your browser to cancel your account. Remember, the cancellation of your account is not reversible and this link expires after one day so nothing will happen if it is unused.
Ideally, this value should be a one-word name of your partner organization, without any spaces. However, there are exceptions for Corporate Payment APIs in the case of fund transfers, IMPS, NEFT & RTGS, where HDFC Bank assigns a specific value to be set as the Scope value. It is mandatory to mention the scope value as your application would be rejected without it.
You can refer to this link- https://codebeautify.org/
You can refer to this link- https://www.xml.com/pub/a/2001/08/08/xmldsig.html
Yes, the platform will show the "Signature verification failed" error if the signed payload value and original payload value have minor differences.
You can refer to this link-https://www.base64encode.org
You can refer to this link- https://8gwifi.org/RSAFunctionality?keysize=2048
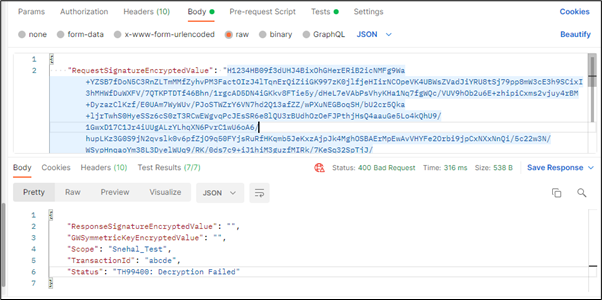
No, you can not use No Padding for both encryption and decryption algorithms as that would result in a "Decryption failed" error.
Yes, algorithms mentioned in HDFC Bank's user manual are as per HDFC Bank API security guidelines and have to be used in that exact manner. To put it simply, symmetric encryption uses the AES/CBC/PKCS5Padding algorithm, while asymmetric encryption uses RSA/ECB/PKCS1Padding.
Yes, it is mandatory for Partners to utilize a 32-byte random (alpha-numeric) key to symmetrically encrypt the complete API request payload. A new value of this 32-byte random key needs to be generated for each API requested by the Partner.
Yes, it is mandatory to set a unique transaction ID every time to identify a JSON wrapper request.
HDFC Bank's SSL certificate public key is required. Any other public key will result in a "Decryption failed" error.
IV stands for Initialization Vector, which needs to be passed by appending the same at the beginning of the original request payload, before performing the encryption. If the IV is not being used for AES encryption, then 16-byte random characters need to be specified at the beginning of the original request payload before performing the encryption.
The following special characters are restricted as API requests with these characters trigger Code Injection or SQL Injection validations on the API Platform. It is recommended that the Partners replace these special characters with a space.
& (ampersand)
' (apostrophe)
, (comma)
. (full stop)
- (hyphen)
/ \ (forward and backward slash)
! (exclamation)
You can use the Client ID as Username and the Client Secret as Password.
No, Partners need to generate a new OAuth token for every request.
No, all HDFC Bank APIs do not utilize OAuth. HDFC Bank has classified a few APIs under the high criticality section, especially APIs that involve financial transactions and only those APIs utilize OAuth. A separate API has been published for generating a one-time-use OAuth token, which requires valid values for Client ID and Client Secret to generate a token. The token needs to be sent as part of the request of the main API.
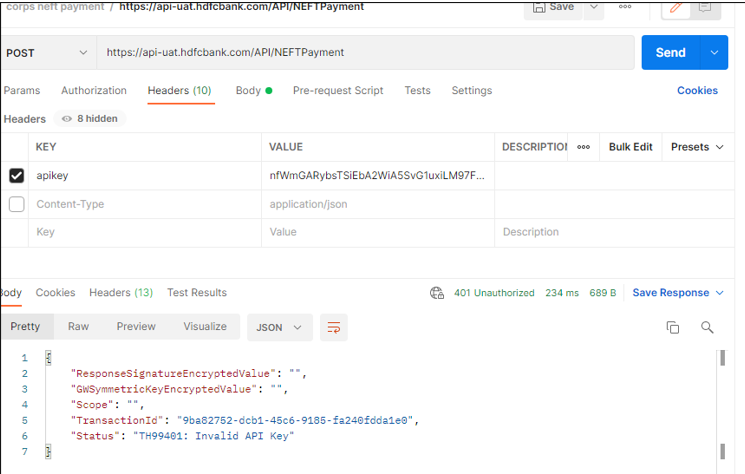
If the Partner does not provide an API Key or mistakenly provides an incorrect one, then they receive an error stating "Invalid API Key".
You can specify "application/json" under the content type field.
You can refer to this link- application/www-form-url encoded
Once you have registered, you can log into the HDFC Developer Portal to access the technical documentation on our API Products. Go to the API catalog section of the portal for further details.
Once you create an account on the HDFC Bank Developer portal, you can access the Sandbox. There you can make API calls that mimic our production environments. In the Sandbox, we use mock data so that you can prototype your application as if it were the real thing.
Our API Catalog page can show you what APIs are available segregated the product basis. If you have a really strong business case for a new API, we’d love to hear about it.
Think of an application as your API key and secret management. It’s enables you to retrieve access tokens. You can register as many as you like.
Error 4xx
This series mainly addresses errors occurring on the client side.
• Bad request- 400
• Unauthorized- 401
• Forbidden- 403
• Not found -404
• Conflict-409
• Unsupported media type-415
Error 5xx
A. This series mainly addresses errors occurring on server side.
B. Internal Server Error-500
C. Not implemented-501
D. Bad Gateway-502
E. Service unavailable-503
F. Gateway timeout-504
The HDFC Developer Portal is a platform for subscribing APIs, testing your product journeys in our sandbox and launch your products by partnering with HDFC Bank. Corporates, Fin-techs, Start-ups, E-Commerce Players, BFSI companies and developers interested in using these APIs can register for the portal and test the APIs in a secure sandbox environment.
API stands for Application Program Interface or Application Programming Interface. It is a set of commands, functions and procedures programmers can use when building applications. HDFC Bank's APIs allows programmers to use pre-defined functions to interact with the Bank's applications. One application can use an API to make a standardized request to another application and get the other application to take the input, perform an operation and return standardized output back to the original application.
To register, visit the registration page.
Go to the login page and click on ‘Forgot password?’. Make sure to enter correct username or email address. You will receive an email to reset your password.
HDFC Bank welcomes innovation and constantly continues to change the way we do business. With Embedded Finance and Open Banking taking central stage in current Banking Environment, it is imperative that we open up our API stack for the new age businesses take advantage of our offerings. Help us do things better. Help us help you.
You can test our APIs and your user flow in our sandbox environment before implementing
Request you to reach out to your dedicated RM for sharing details on your journeys and APIs that needs to be consumed. He shall update you on commercials, if any. Or you can reach out to us via contact us option to address your queries
A Partner's SSL public certificate should have at least 1 year of validity.
After activation, you can simply log in to your account by clicking on the link you receive in your email or copy pasting it to your browser. This is a one-time login link that will redirect you to a page where you can set your password. Once you have set a password for your account, you can log in by clicking on the other link provided in the same mail, and entering your username and newly set password
Once you have registered on our portal, your application will be pending for approval. Post approval, you will receive an email containing your password, information on how to log in and other details
Use the following parameters for Oauth Token generation
URL : https://api.hdfcbank.com/auth/oauth/v2/token
Params :
- grant_type - client_credentials
- scope – ( from portal )
Authorization :
Basic Auth -
- Username- Consumer key (from portal)
- Password - Consumer Secret ( from portal)
Headers:
Content-Type - application/x-www-form-urlencoded
Login to Developer Portal.
Navigate to API Catalog and select the category of the API Products.
Then Open the API Product and click on docs link of a particular API to download the technical document of that API.
Login to the Developer Portal.
Navigate to the API Catalog and select the category of the API Products.
Then Open the API Product and click on TryItOut of particular API and click on usermanual link to download.
Currently there is no process of updating a partner email ID in the portal.
a) A partner will need to raise the request to change the developer email. The request needs to be routed to the bank team.
b) Upon receipt of your request the technical team will update.
a) Login to Developer Portal.
b) Navigate to Launchpad and edit the app to update the certificate.
c) Update the leaf certificate in leaf certificate field. Then submit the app.
d) Confirm app submission
a) Login to the Developer Portal.
b) Navigate to Launchpad and select “Edit” to update the IP.
c) Update the IPs in IPs field. Then submit the app.
Updated IP will be reflected once it is approved by the Bank team.
The following are the steps for High encryption
HIGH:-
1) Signature algorithm RSA SHA 256 -> payload -> (using)Clients private key -> signed payload (Signature)header.payload.signature
2) Generate random alphanumeric 32 bytes string (Symmetric Key) example: vtxvqwvxuyvqwxbwbxibchbwcibwcwbic
3) IV+Signature encryption <-->(using) Symmetric Key --> Encryption Algorithm (AES/CBC/PKCS5) byte[] <--> base64encoding ==> RequestSignatureEncryptedValue
4) Symmetric Key encryption<--> (using) hdfc publickey (api-uat.hdfcbank.com.cer) --> Encryption Algorithm (RSA/ECB/PKCS1) byte[]<--> base64encoding ==> SymmetricKeyEncryptedValue
The following are the steps for a Medium encryption:
MEDIUM:-
1) Generate random alphanumeric 32 bytes string (Symmetric Key) example: vtxvqwvxuyvqwxbwbxibchbwcibwcwbic
2) IV+Payload <-->(using) Symmetric Key --> Encryption Algorithm (AES/CBC/PKCS5) byte[] <--> base64encoding ==> RequestEncryptedValue
3) Symmetric Key encryption<--> (using) hdfc publickey (api-uat.hdfcbank.com.cer) --> Encryption Algorithm (RSA/ECB/PKCS1) byte[]<--> base64encoding ==> SymmetricKeyEncryptedValue
For API’s with Low risk, no encryption is required.<>
We encounter this error when special characters are used in request payload.
*Characters that trigger SQL Injection errors are' # --
*Words that trigger SQL Injection error :- delete, drop table, alter table, insert, shutdown, update, select, exec , echo, config, set, printenv ,
*Characters that trigger Code Injection error are *()<>^`&; *()<>^`&;`'";|&>\
*Words that trigger Code Injection error :- applet, embed, iframe, ilayer, html, body, object, script, img, meta, style, ancestor-or-self, descendant-or-self, following-sibling